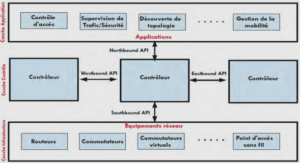
Problem statement and motivation
In the new global information technology, trust has become a central issue for many organizations and individuals [14]. Evidence suggests that trust is among the most important factors for establishing a relationship and adoption of technology such as cloud computing [14]. Although, more than two decades has elapsed from the first day of introducing cloud computing, unlike the various evolutions and progressions in this technology, trust and trustworthiness are still major concerns and open issues [14]. There is a growing body of the literature that recognizes the importance of trust and evaluating the trustworthiness of the cloud service providers (e.g. [21-23]) [14]. The main challenge faced by many researchers is that the notion of trust is combined with uncertain concepts and at the same time associated with functional and non-functional requirements [14]. This causes that trust in cloud computing remains an obstacle for cloud technology adoption [14]. On the other hand, there is no consensus based rule or agreed standard to evaluate trust in cloud environments [13, 14, 20].
In cloud computing standards, the key characteristics of cloud have been defined and several concepts related to this technology have been explained [14, 24]. However, there is no clear path to guide stakeholders or individuals toward a trustworthy cloud service provider [14]. To identify the influential characteristics that cover different aspects of trust and users’ requirements, many researchers proposed several trust characteristics, but they are not sufficient enough to boost users’ confidence in applying cloud technology [14]. For example, in the majority of scientific publications, security is first and foremost trust characteristic that needs to be tackled from different perspectives (e.g. [25]) [14]. Undoubtedly, security is a major challenge in cloud computing, but it is important to bear in mind that it is one of the various aspects of trust [14]. Moreover, a significant part of a reasonable evaluation of trust in cloud environments pertains to evaluating the measures of quality characteristics that are proposed as trust characteristics [14]. Most studies in the field of evaluating trust in cloud computing have only focused on the insufficient set of characteristics with inappropriate measures [14].
In addition, these measures are not necessarily based on the quality standards, which may lead to incomprehensive evaluation of cloud services [14]. Hence, extensive research has shown that there is an urgent need to address these trust characteristics along with their measures which can be supported scientifically [14]. Regarding the aforementioned criteria, a broadly acceptable cloud trust model is required to aid the assessment of cloud services that are proposed by cloud service providers. Despite the fact that several approaches have been identified to design a cloud trust model for assessing the trustworthiness of a cloud service provider, further research is needed to design a broadly acceptable cloud trust model that can evaluate various aspects of cloud services. Therefore, the aim of this thesis is to design a broadly acceptable cloud trust model that to the best of our knowledge would be the first cloud trust model that can cope with different cloud service users with different requirements and at the same time can assess standard trust characteristics. Figure 0-2 illustrates the limitations which are addressed in this research work.
The structure of this thesis
The overall structure of this research project takes the form of 11 chapters, including: Chapter 1 presents the literature review on fundamental concepts, main definitions and provides a critical appraisal of previous works in the domain of trust in cloud computing. In this chapter, the shortcomings of existing cloud trust models are discussed and their methodologies are analyzed. Further, this chapter explains the common features of existing cloud trust models which are proposed by several researchers. This can be considered as a guideline to determine a proper methodology to propose a unique cloud trust model. Chapter 2 discusses the methodology of this research in which there are five main phases; analysis phase, matching phase, tracing phase, development and exploitation. The details of these phases are described in this chapter. Chapter 3 presents an overview of the ISO/IEC standards applicable in cloud computing technology. The purpose of this investigation is to match the relationship between existing system and software quality standards and cloud computing technology to extract standard characteristics. In addition, this chapter compares trust characteristics extracted from the literature to analyzed standards to propose the key trust characteristics in cloud computing.
In this chapter we try to present the trust characteristics that are commonly recognized in the literature and by the help of existing ISO/IEC standards, we identify their key subcharacteristics. Chapter 4 discusses the measures of extracted trust characteristics explained in chapter 3 based on ISO/IEC 25022 and ISO/IEC 25023. These measures are matched with the sub11 characteristics of the specified trust characteristics to contribute a more comprehensive cloud services assessment. Chapter 5 describes the three cloud service models (IaaS, PaaS and SaaS) and presents their important features. In this chapter IaaS, PaaS and SaaS are compared together and their main similarity and major difference are identified to be able to verify the applicability of trust characteristics measures (in chapter 6) in cloud environments correctly. Chapter 6 verifies the feasibility of trust characteristics assessment by different categories of cloud users in cloud environments. In this chapter, cloud users are categorized into three groups: individual, organization and cloud service provider (the owner of the cloud service). The details of these categories are discussed in this chapter. Chapter 7 discusses the main results of the two stages of tracing phase explained in the chapters 5 and 6 and presents the separated models of trust characteristics for the three identified categories of cloud users and the evaluation functions of the proposed measures. These models are the essential parts that later will be applied in certain phases of ED-BeCT. Chapter 8 explains the phases of the ED-BeCT in detail. In this chapter, the equations for
Analyzing trust characteristics applied in cloud environments
There is no doubt that cloud trust model characteristics are mostly based on customer requirements. Furthermore, to the best of our knowledge there is no specific standard or agreed rule to select those characteristics and there is not much research in this area. In all the existing trust models, the main concern is finding the way of calculating trust value rather than standardizing trust characteristics that should be evaluated by the trust model. In this section, we analyzed the trust characteristics which are covered by existing trust models with respect to the criteria defined in the cloud computing standards. As it was found during the presented analysis, most of the cloud trust models (CTMs) such as the ones proposed in [26-36] consider security as a main trust characteristic. Shaikh et al. in [37] proposed a trust model to evaluate the security strength of cloud computing services. The author in this paper considered nine security characteristics that in his opinion were necessary and sufficient but in reality they were found insufficient based on the dynamic nature of cloud and the criteria in cloud standards. Ghosh et al. in [38] proposed a risk estimation while interacting with a cloud service provider by combining the trustworthiness and competence of a cloud service provider.
In addition, there are several papers for evaluation of the CTMs such as [39] that are based on the security while the other aspects of trust are ignored. Abdallah, E.G, et al. in [40] introduced a trust model for cloud-based applications. This model addressed the four components of security characteristics and mechanism (integrity, availability, privacy and access control) for both man-in-the-middle and man-at-the-end attacks. In this model the author fails to acknowledge the significance of other subcharacteristics of security (such as confidentiality and non-repudiation) as are defined in ISO/IEC 25010 [1]. Singh et al. in [41] proposed a multidimensional trust model that integrates multiple trust characteristics. Cloud Data Trust and Reputation of the Service are considered as two aspects of trust to calculate the trust value. Data Processing, Data Transmission, Data Storage, Data Privacy and Data Security are covered by the cloud data trust and availability, reliability, Turnaround Time, and Service Use Factors are covered by reputation of the service. However, in [11] trust evaluation is just based on four factors: Availability, Reliability, Turnaround Efficiency and Data Integrity which are considered by the authors the credential characteristics.
These models might have been much more convincing if the authors had included all the defined characteristics along with their sub-characteristics in quality standards to evaluate trust Li et al. in [42] proposed a trust model to assess servers dynamically and select high-quality cloud services based on the user’s requirements. This model integrated multiple trust characteristics and considered the three following characteristics to guarantee service level agreement: security, availability and reliability. However, the considered characteristics may not be adequate to boost users’ confidence. In [43] the trust factors that impact the cloud adoption are introduced as Security, Usability, Reliability, Auditability, Interoperability, Accountability, Controllability and Company Scale. Garg et al. in [44] introduced a framework that measures the quality of the cloud services and proposed a ranking mechanism. This mechanism utilizes AHP (Analytic Hierarchy Process) to rank the cloud services based on multiple-KPIs (Key Performance Indicators). Any number of characteristics can be deployed in AHP but Accountability, Agility, Cost, Performance, Assurance, Usability, Security and Privacy are the suggested mechanism. Obviously, researchers in these articles have not treated trust characteristics in much detail and also the related sub-characteristics identified in quality standards are not taken into consideration.
INTRODUCTION |