- Tuesday
- July 23rd, 2024
- Ajouter un cours

........ Checklist for TS Licensing Tasks to be completed to install and configure TS Licensing: Review prerequisites for installation Install the TS Licensing role service Activate the Terminal Services license server Install TS client access licenses (TS CALs) Configure the...

....... What Is NAP? Enforces client health before allowing access to the network Can allow access to remediation servers Has various enforcement mechanisms Controls network access for noncompliant computers Does not block intruders or malicious users Scenarios for Implementing NAP...
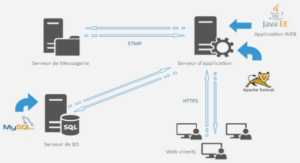
Sommaire: Cours les cahiers du programmeur java 1.4 et 5.0 AVANT-PROPOS 1. PRÉSENTATION DES ÉTUDES DE CAS Applications isolées Carnet d’adresses Calcul des mensualités d’un emprunt Forum de discussion Principales fonctionnalités Architecture technique Module de messagerie instantanée (chat) En...

........ Introduction to TS Web Access TS Web Access is a role service that allows you to start RemoteApp™ programs without the need to download or run .msi or .rdp files TS Web Access in Microsoft Windows Server® 2008: •...

.......... Demonstration: Configuring AD DS User Accounts In this demonstration, you will see how to configure AD DS user accounts Default AD DS Groups Default groups are designed to manage shared resources and delegate specific domain-wide administrative roles Account operators...

........ What Is Group Policy? Use Group Policy to: • Apply standard configurations • Deploy software • Enforce security settings • Enforce a consistent desktop environment Group Policy enables IT administrators to automate one-to-many management of users and computers Local...

.......... Challenges of Securing a Windows Infrastructure Challenges of securing a Windows infrastructure include: • Implementing and managing secure configuration of servers • Protecting against malicious software threats and intrusions • Implementing effective identity and access control Core Server Security...

......... Using IP Security Monitor to Monitor IPsec Options for using the IP Security Monitor: • Modify IPsec data refresh interval to update information in the console at a set interval • Allow DNS name resolution for IP addresses to...
Benefits of IPsec IPsec is a suite of protocols that allows secure, encrypted communication between two computers over an unsecured network • IPsec has two goals: to protect IP packets and to defend against network attacks • Configuring IPsec on...