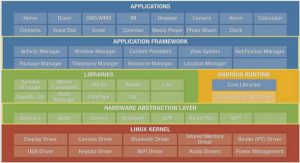
Introduction
What is a Secure Site?
Windows NT Security
User Accounts
Understanding Rights in Windows NT
Authentication
Accessing Windows NT Resources
File Access
System Registry Access
Authenticated Protocols
Rights and Policies
Internet Information Server Security
IIS Anonymous User
How Secure is Anonymous Access?
NT Challenge/Response Authentication
Basic Authentication
HTTP Authentication
Securing Pages
Securing Pages Using NT File Permissions
Securing Pages Using HTTP
Impersonation
Delegation
COM Components
DCOM Components
Threading
Visual Basic 5.0 Components
Secured Communications and SSL
IIS 3.0 Security Flowchart
SQL Server Security
SQL Security vs. NT Security
Standard Security
Integrated Security
Mixed Security
SQL Server Protocols
Named Pipes
TCP/IP Sockets
Using SQL Server with IIS
Standard SQL Server Security
Using Other Protocols
Using Integrated SQL Server Security
Introduction
Since the introduction of Microsoft® Internet Information Server (IIS) 1.0, Microsoft® Windows NT® and IIS have and probably always will be bedfellows.
Because the two products are so tightly integrated, working with Active Server Pages (ASP) in IIS 3.0 affords us the same level of security that NT itself offers. The benefit of this is the ability to develop Web sites tightly integrated with the Windows NT security model. The side effect, however, is that in order to develop a secure site one must understand the paradigm that IIS and ASP run under with Windows NT. That is what this article is devoted to.
This article provides an overview of Windows NT security in areas relevant to IIS and Microsoft® SQL Server. After gaining a basic understanding of these three products’ relationships, you will learn how their mutual features are utilized to implement security with Active Server Pages. These topics will not be explored in any more depth than is necessary for understanding the implementation of security with Active Server Pages.
What is a Secure Site?
Security is a broad topic. When implementing a secure site, you need to consider two major areas that surround the topic of security.
1. Controlling who can browse a site.
2. Making sure that information communicated cannot be seen by unwanted observers.
While completely independent of one another, the two can be used in conjunction to provide any level of security desired.
Controlling who can connect to a Web site and access files is handled through a combination of NT security and IIS. After an overview of the topics surrounding security in IIS and ASP, these topics will be addressed with a discussion of how Active Server Pages can be used with either or both of these.
Windows NT Security
The important thing to understand about security in relation to Windows NT is that it is pervasive. This means that anything you do in Windows NT is going to involve some type of security check. If you attempt to access a file, a security check will happen; if you try to log on to a workstation, a security check will happen. When using Windows NT as a desktop operating system, these security implications are most commonly invisible to us. This is because, in most situations, you will log on to your own machine as an administrator, and, consequently, never stumble into any permissions issues. So, if there is any question in your mind as to what this means, it can be answered in one simple statement: An administrator of a given machine is the “god” of that machine.
User Accounts
If you have ever used Windows NT on a Local Area Network, you have been exposed to more of the security involved in NT. All security in Windows NT revolves aroun d user accounts. Depending upon whether you are logged into a LAN or not will determine which user account you will be using. This can get a little confusing, but it is important to differentiate between the two. In a stand-alone machine scenario, all of your privileges to that machine are determined by your Local User Account. For example, this includes all file access, the ability to install programs properly, and the ability to log on at all.
Local Groups vs. Domain Groups
All Windows NT machines come with a set of predefined groups set up in the user manager. These groups are based around a set of common roles users generally play when working with a computer. Each group has a level of privileges and rights set up for them based around these roles. For example, the Power User group has more rights and privileges than the Users group. Therefore, Local Groups serv e two roles.
From an administrative standpoint, they allow an administrator to organize his or her users into groups, while also granting them privileges and rights at the same time.
Domain Groups differ from Local Groups in one major way. A Domain Group serves only as a means to organize users. The implications of this are very subtle, so consider carefully, that this means that making a user an administrator..
Implementing a secure site with ASP ( 1737 KO) (Cours DOC)